JWT - Refresh Token and Access Token
Introduction :#
JWTs (JSON Web Tokens) provide secure, stateless authentication. Access Tokens are short-lived, granting quick access to resources, while Refresh Tokens are long-lived, allowing users to renew access without re-login. This combination strengthens security and enhances user convenience.
Using JWT For Authentication#
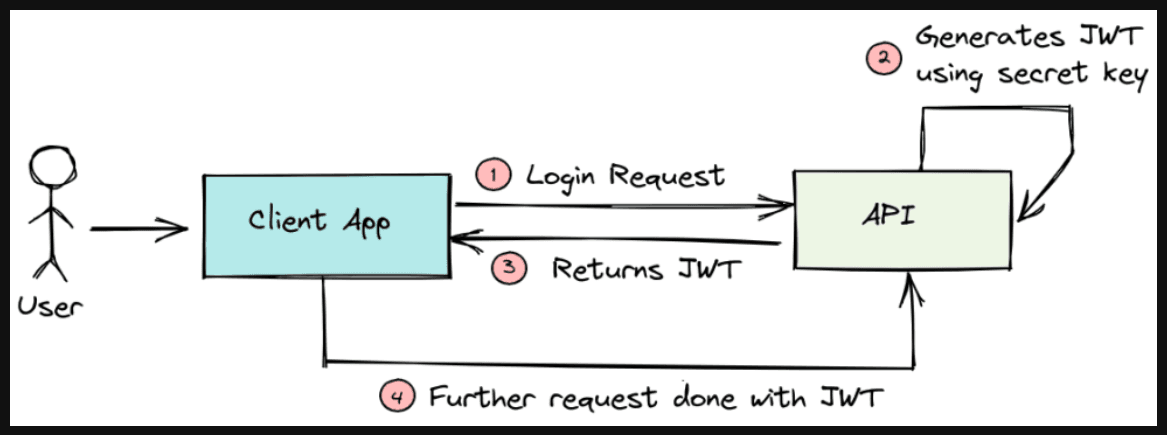
This diagram illustrates a basic flow of JWT (JSON Web Token) authentication(Before using Refresh token):
- Login Request: The user first sends a login request from the client application to the API, usually with credentials like a username and password.
- JWT Generation: Upon successful authentication, the API generates a JWT using a secret key. This JWT contains encoded information about the user and is signed to ensure its authenticity.
- Return JWT: The API then returns the generated JWT to the client application. This token serves as proof of authentication.
- Further Requests with JWT: For subsequent requests to the API, the client app includes the JWT in the request headers. The API validates the JWT to authorize the user and processes the request accordingly.
This flow helps in maintaining a stateless, secure communication between the client and the server.
Issues with JWT Access Tokens#
1. Extending User Sessions Without Reauthentication:
- Problem: Since JWT Access Tokens are short-lived for security reasons, they expire quickly. Without a Refresh Token, users would need to reauthenticate frequently, which disrupts the user experience.
- Solution: A Refresh Token allows the server to issue a new Access Token without requiring the user to log in again, keeping the session active and smooth.
2. Minimizing Risk of Token Misuse:
- Problem: If a long-lived Access Token is compromised, it can be misused until it expires, posing a security risk.
- Solution: By using a short-lived Access Token combined with a Refresh Token, even if the Access Token is compromised, its usefulness is limited. The Refresh Token is stored more securely and is only exchanged for a new Access Token, reducing the chance of exposure.
3. Improved Security and Control:
- Problem: JWT Access Tokens cannot be revoked or invalidated before their expiration. This makes it challenging to manage sessions, especially if a token is compromised.
- Solution: With a Refresh Token, the server can issue new Access Tokens and revoke old ones if suspicious activity is detected, giving more control over session management and improving overall security.
The solution is to use Two Tokens:
Access Token(for 5mins - 10mins)
This is like a single ride ticket. It lets you go on one ride, but once you’ve used it, it’s no longer valid. It only works for a short time, just like how an Access Token is used to access your account or a service for a limited time.
Refresh Token(for next 6 months)
This is like an all-day pass. After your ride ticket (Access Token) expires, you don’t have to buy a new one. Instead, you use your all-day pass to get a new ride ticket. The Refresh Token works the same way—it lets you get a new Access Token when the old one expires, so you can keep using the service without logging in again.
Using Two Tokens instead of One#
Using two tokens, an access token and a refresh token, enhances both security and user experience. Access tokens are short-lived, limiting the damage if compromised since they expire quickly. Refresh tokens are long-lived and only used to obtain new access tokens, reducing the exposure of long-term credentials and allowing them to be stored more securely, such as in HTTP-only cookies. Additionally, even if the access token expires, the refresh token can be used to maintain session continuity without disrupting the user.

The diagram illustrates the interaction between a client, server, and token service using both an Access Token and a Refresh Token to enhance security and user experience.
Conclusion#
This article explains the use of JWTs, where Access Tokens are short-lived and provide immediate access, while Refresh Tokens are long-lived, allowing users to renew their Access Tokens without re-login. Using both tokens improves security and user experience by minimizing token misuse and enabling seamless session management.